Admin adaptive MFA
Learn how to set up and use Adaptive MFA policies to enhance the security of your administrative accounts and Strivacity console.
Overview
Adaptive MFA (Multi-factor Authentication) enhances the security of your Admin Console by using a combination of multi-factor authentication and risk analysis techniques.
Login workflow
Strivacity provides several login workflows to choose from depending upon the approach you want to take to authentication.
You can find more information about login workflows here.
Multi-factor authentication
Multi-Factor Authentication (MFA) provides an additional layer of security beyond just a (single factor) username and password-based authentication.
SMS, Voice Call, and email managed service
All SMS, Voice Call, and email services are supported and fully implemented to apply as additional factors right from the start.
Soft token authenticator apps
Soft token authentication support allows your administrative staff to use the one-time passcode generator app of their choice.
FIDO2-based authentication
FIDO2 is a standards-based protocol that enables device-based authentication. Compared to the rest of the existing authentication methods, device-based authentication requires the least effort from users, which also equals less friction during enrollment and login journeys.
You can find more information about multi-factor method configuration.
Risk analysis techniques
Strivacity's Adaptive MFA policies include several risk analysis techniques that can adjust and enhance your administrators' registration or login journey.
Optimized outcomes
Deny authentication or registration
If the risk level of an authentication is deemed to be too high, the request can be denied.
Step-up authentication
If risk is detected during authentication, a step-up authentication can be triggered.
Redirection
If risk is detected during authentication, the administrator can be redirected to an alternative URL (web page).
Fraud detection tools
Adaptive MFA policies come with out-of-the-box fraud mitigation tools to protect your brand from fraudulent actors.
Bot detection
Login attempts from malicious bots comprise a little over a third of all login attempts on the web. You can set up blocking or step-up rules to deal with the detected threats.
Anonymous proxy / Tor detection
Online identity concealment makes it impossible to accurately verify these users' geographical whereabouts.
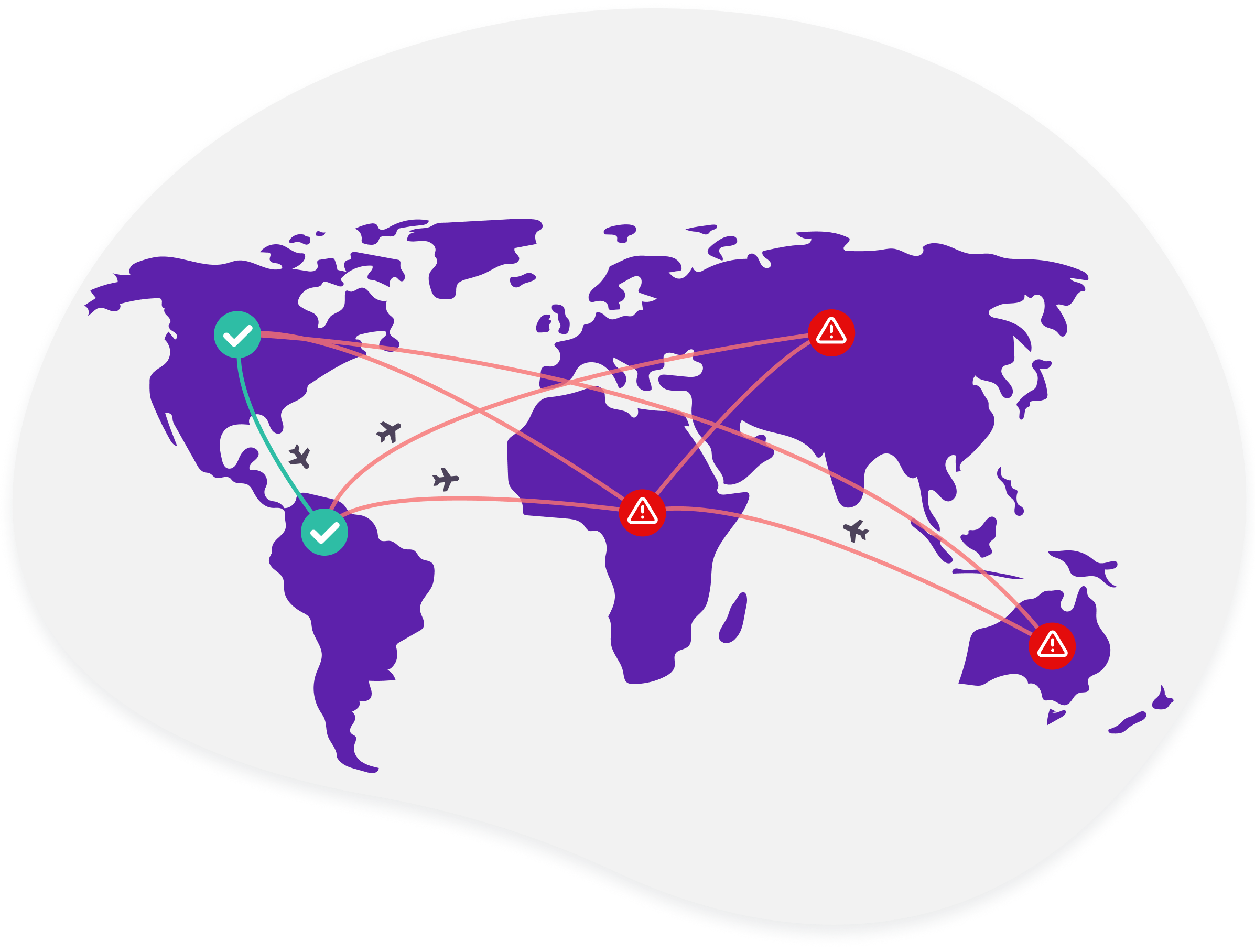
Improbable travel detection
Improbable travel may be a sign of account takeover: malicious actors engaged in account takeover activities are often not logging in from the same location as the user usually does. To mitigate the risk of account takeover fraud, an additional factor can be requested if an improbable travel event is detected.
Behavior analytics
Many users login in from the same location or a similar time of day or week. You can enable behavior analytics to identify trusted customer behavior.
Learn more about how adaptive rules and fraud detection tools can be combined to mitigate potential risks.
Updated 4 months ago
