Adaptive multi-factor authentication
Learn how to setup and use an Adaptive MFA policy to enhance the security of your portal or web application.
Overview
Adaptive MFA (Multi-factor Authentication) enhances the security of your portal or web application using a combination of risk analysis techniques and multi-factor authentication.
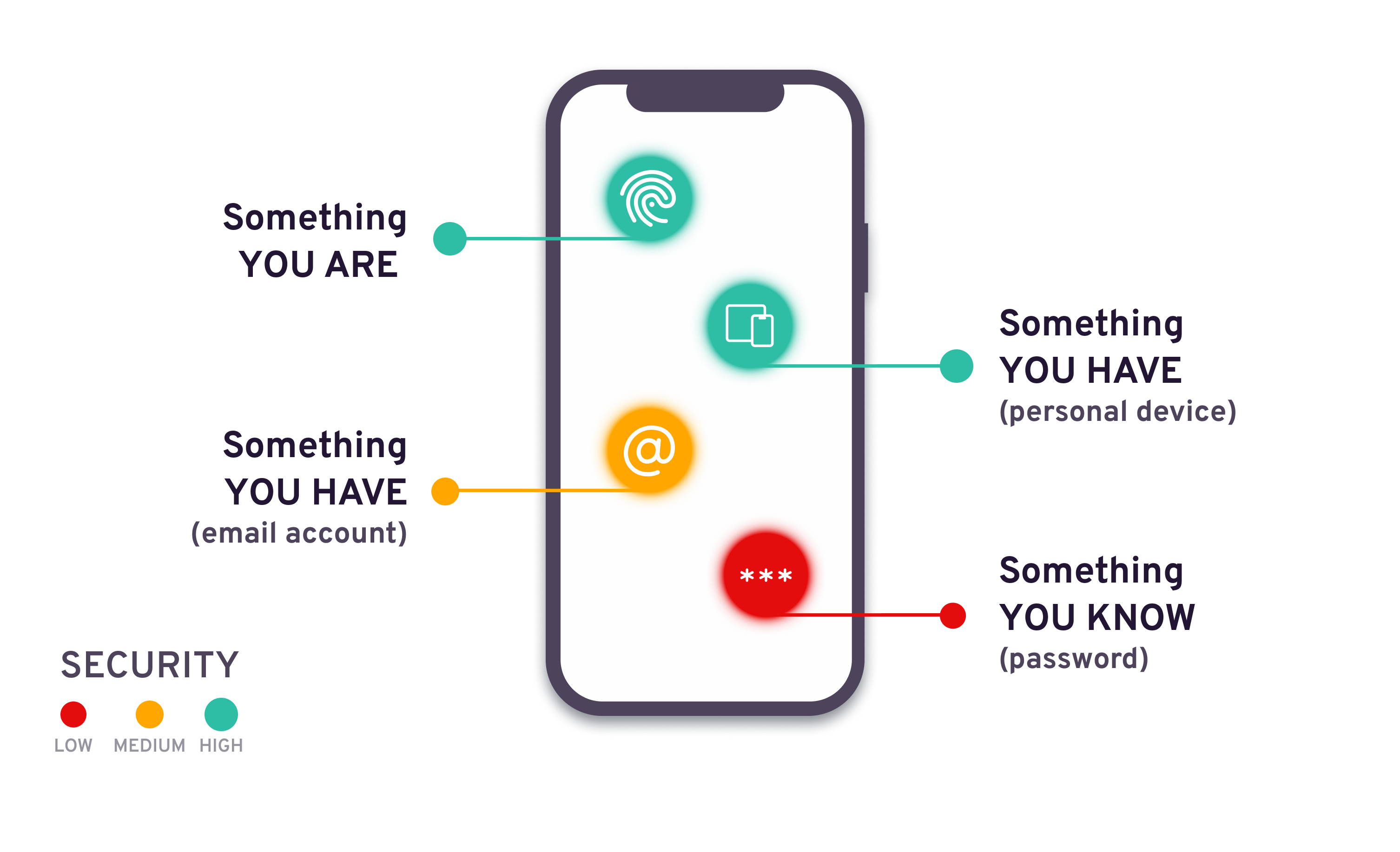
An Adaptive MFA Policy contains the following settings:
- Login workflow
- Multi-factor authentication
- Risk Analysis Techniques
Learn how to
- Create an Adaptive MFA Policy
- Edit an Adaptive MFA Policy
- Delete an Adaptive MFA Policy
- Assign an Adaptive MFA Policy to an Application
Login workflow
Strivacity provides several login workflows for you to choose from depending upon the customer journey that you wish to create.
Because a login workflow can be defined for an Adaptive MFA policy, it means that you can have multiple applications each with its own Login Workflow, giving you flexibility to provide different customer journeys per application.
Multi-factor authentication
- SMS and voice call managed service
- Email managed service
- Soft token authenticator apps
- FIDO-based authentication
Multi-Factor authentication (MFA) provides an additional layer of security beyond just a (single factor) username and password-based authentication.
Multi-Factor authentication protects your customers against threats such as,
- Account takeover
- Unauthorized account access
- Fraudulent transactions
- Account hijacking
Strivacity provides the following MFA methods:
| Method Type | Security Posture | Ease of Adoption | Coverage | Usability |
|---|---|---|---|---|
| Password | Weak | Easy | Broad | Easy |
| Voice Call OTP | Moderate | Easy | Broad | Medium |
| SMS OTP | Moderate | Medium | Broad | Medium |
| Email OTP | Moderate | Medium | Broad | Medium |
| SMS Magic Links | Strong | Easy | Medium | Easy |
| Email Magic Links | Moderate | Easy | Broad | Easy |
| Google Authenticator or other Soft Token | Strong | Medium | Medium | Medium |
| FIDO2 Platform Biometric Authenticator | Strong | Easy | Medium | Easy |
| FIDO2 Security Key | Strong | Medium | Broad | Easy |
SMS and voice call managed service
Strivacity provides a fully included and managed SMS and Voice Call service with global coverage. No further configuration or need to subscribe with a third-party service provider is required - meaning that there is nothing additional to configure or set up to start using Strivacity supported phone-based Multi-Factor Authentication methods.
See Customizing SMS Templates for more information on how to use your own branding and customize the way in which SMS messages are sent.
Email managed service
Strivacity provides a fully included and managed Email service. No further configuration or need to subscribe with a third-party service provider is required - meaning that there is nothing additional to configure or set up to start using Email notifications or supported Email-based Multi-Factor Authentication methods.
See Customizing Email Templates for more information on how to use your own branding and customize the way in which Email messages are sent.
Soft token authenticator apps
Soft token authentication support allows your customers to use the one-time passcode generator app of their choice.
Customers download the authenticator app to their phone, enroll the application in their self-service portal, and use the available temporary one-time passcode to authenticate. With only having to install an application, customers don’t need to provide their email address or phone number to receive passcodes. Automatic token renewal is not only secure but supplies customers with new passcodes without needing them to send a request.
FIDO2-based authentication
FIDO2 is a standards-based protocol that enables device-based authentication. Leveraging their everyday devices, users can authenticate with biometrics – fingerprint, face-scan, or voice recognition – or a physical security token of choice.
Ever since the FIDO alliance entered the scene, more and more devices ship with FIDO-compliant platform authentication systems, such as Android, Windows Hello, Apple Touch, and Face ID or support roaming authenticators such as Yubikey and Google security keys.
Compared to the rest of the existing authentication methods, device-based authentication requires the least effort from customers, which also equals less friction during enrollment and login journeys.
You can tap into the secure and convenient device-based authentication solutions customers already have at their command with Strivacity FIDO authentication support.
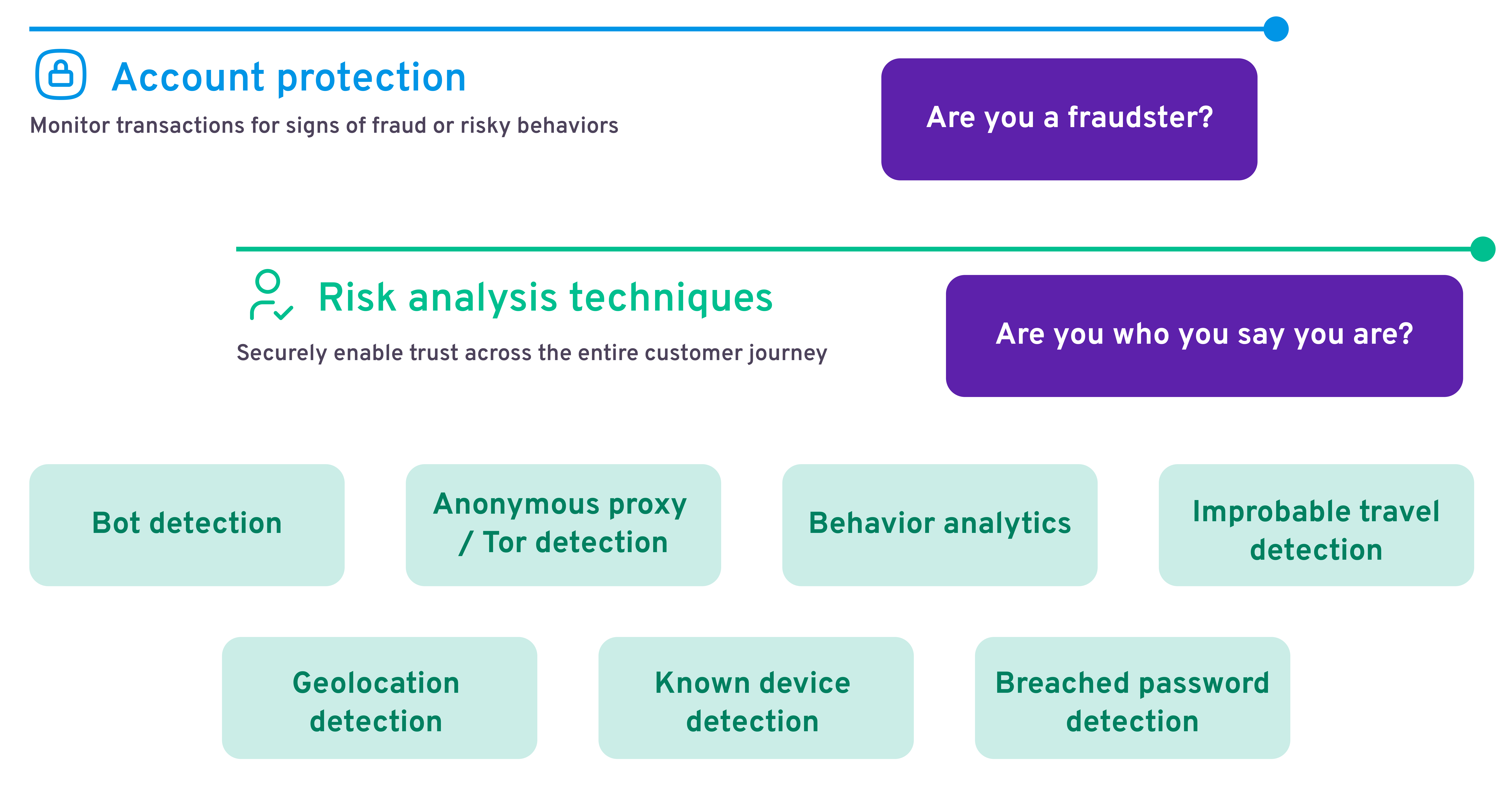
Risk Analysis Techniques
Strivacity's Adaptive MFA policies include several risk analysis techniques that can adjust and enhance your customer's registration or login journey.
- Optimized Outcomes
- Fraud detection tools
- Account lockout
- Geolocation Detection
- Improbable Travel Detection
- Known Device Detection
- Breached Password Detection
Optimized customer outcomes
Strivacity includes several workflow options that can be used where they make sense during registration, login, or password reset.
| Outcome | Description |
|---|---|
| Step-up Authentication | When risk is detected during authentication, a step-up authentication can be triggered. This only applies where Multi-Factor Authentication is configured and will require the customer to respond to an Multi-factor Authentication challenge. |
| Deny Authentication or Registration | When risk is detected during authentication (log in), or during self-service registration, the request can be denied, meaning the customer will not be allowed to proceed because the risk level is deemed to be too high. |
| Redirection | When risk is detected during authentication (log in), or during self-service registration, the customer can be redirected to an alternative URL (web page) of the admin users choosing. |
Fraud detection tools
Adaptive MFA policies come with out-of-the-box fraud mitigation tools to protect your customers and brand from fraudulent actors.
Bot detection
Login attempts from malicious bots comprise around 34% of all login attempts on the web. Strivacity's bot detection shields your brand from unwanted consumer bots by analyzing the IP address of authentications and registrations to differentiate between human and non-human traffic.
You can set up blocking or step-up rules to deal with the detected threats for logins, and blocking rules only for registrations. Each rule offers two levels of risk mitigation: normal and high. Pick the protection level that's best for your situation.
Anonymous proxy / Tor detection
Some users hide behind an anonymous proxy server or Tor exit node to conceal their real IP addresses. This makes it impossible to accurately verify these users' geographical whereabouts.
Strivacity's anonymous proxy detection allows you to be confident that only customers with a traceable online presence will have access to your applications. It does this by halting requests coming from hidden IP addresses before users can continue to your services.
You can choose to block or step-up customers who try to log in from anonymous proxy servers or Tor exit nodes.
Behavior analytics
Many customers login in from the same location or a similar time of day or week. Strivacity's behavior analytics uses machine learning to analyze time and location data to reduce friction in your customer's login experience while still providing the high-level security everybody expects.
You can enable behavior analytics in your applications to identify trusted customer behavior. If customers log in from their usual location and time, they will be stepped down from an otherwise required additional factor of authentication.
Account lockout
Account lockout can mitigate any attack that tries to take over accounts with repeated password or temporary passcode attempts, such as brute force attacks, dictionary attacks, or credential stuffing. You can significantly enhance the security of your customer accounts by finding the right combination of limited attempts and account lockout duration.
Improbable travel detection
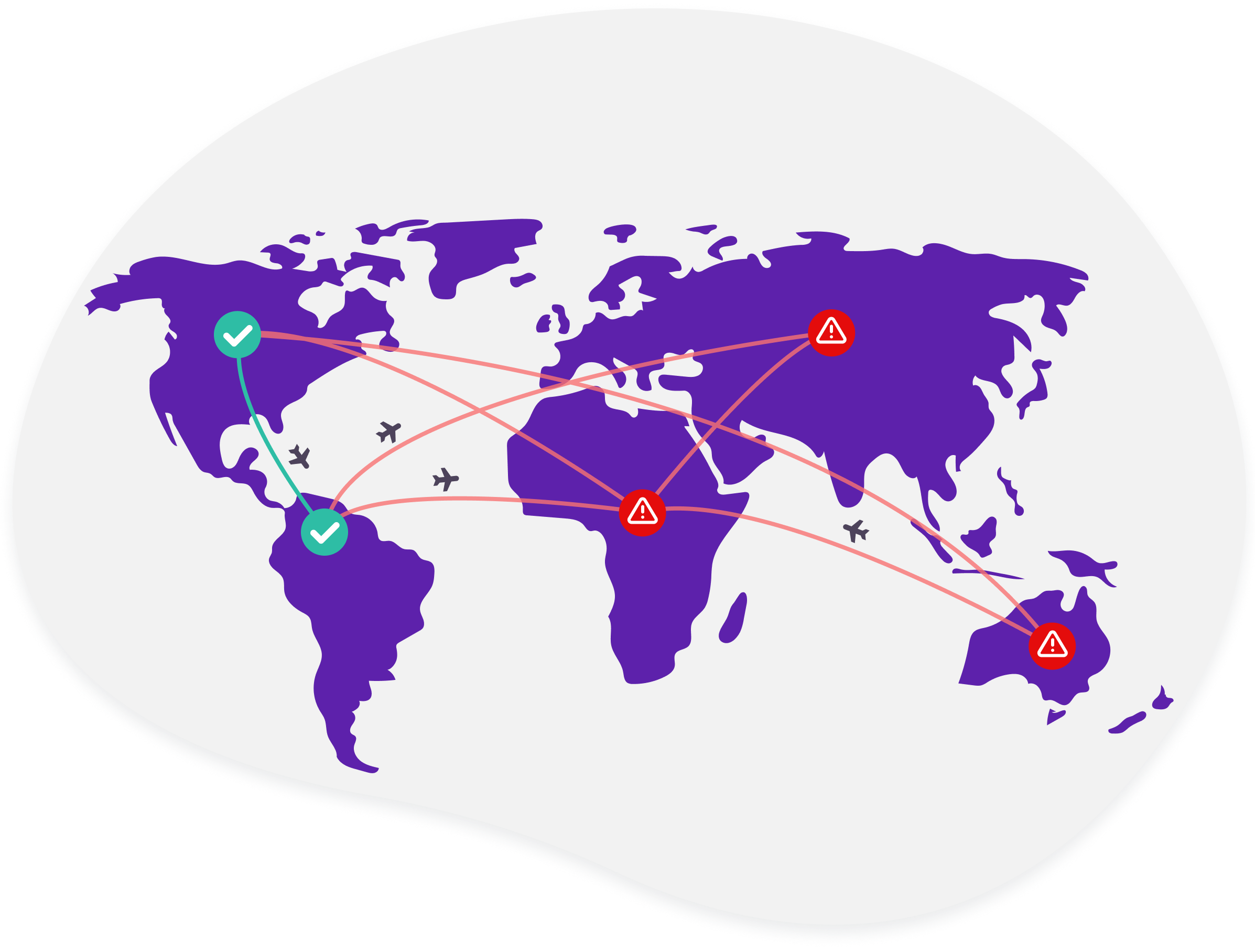
Malicious actors engaged in account takeover activities are often not logging in from the same location as a customer. Strivacity's improbable travel detection combines time/date information with a customer's past and current location to perform a travel velocity calculation - put simply 'could a customer have traveled from point A to point B within the period of time between logins? If 'yes' then the login may be legitimate. If 'no' then the login is suspicious and some action should be taken.
Improbable travel detection protects against account take over without compromising a customer's login experience. It effectively denies access to an attacker that may have attempted to compromise a customer's account.
With improbable travel detection you can:
1) Step-up authentication - if multi-factor authentication is enabled and an existing customer logs in from a location and the likelihood of that distance traveled from the last location seems low, you can step up the customer and ask them for an additional factor as an additional step of verification.
Geolocation detection
Strivacity's geolocation detection resolves IP addresses to physical locations using a highly accurate and frequently updated resolution database.
Why is this useful? geolocation detection allows brands to specifically allow or deny customer registration or logins from any geography that they do or do not want customers to use their application or website. This helps reduce attack surface and provides great assurance to any requirements or law around where an application or website can be accessed from.
This capability allows an admin to change the customer journey based on specific locations at a granular level - the Entire World, Country, State, and City levels - with worldwide coverage.
When configuring geolocation detection, the most restrictive options will always apply. For instance, if you deny registration/authentication from the UK (Country), and then allow registration/authentication from Sheffield (a City within the UK) then any registration or authentication requests from Sheffield will still be denied.
With geolocation detection you can;
1) Allow registration/authentication - the ability to define an allowed list of physical locations that a customer can self-register from or log in from.
2) Step-up authentication - if multi-factor authentication is enabled and an existing customer logs in from a location that you deem risky, you can step up the customer and ask them for an additional factor as an additional step of verification.
3) Redirect registration/authentication - the ability to redirect any customer registration or authentication to a URL of your choosing if the customer is in a specific country/state/city.
4) Deny registration/authentication - the ability to deny any customer registration or authentication from a location that you deem risky.
Known device detection
Strivacity known device detection uses device recognition techniques and a browser cookie to remember a known device upon a successful authentication using Adaptive MFA.
Once a user has been verified and the cookie stored then they will not be asked to provide another Multi-factor Authentication method until:
1) The known device lifetime (default is 30 days and can be configured in the Adaptive MFA policy) expires because the customer has not logged in
2) Other risk is detected via any of Strivacity's other risk analysis techniques. In this situation, the existing known device cookie is revoked when the customer is stepped up
This approach helps ensure a good balance of customer experience and risk analysis. Strivacity will only prompt the customer again for a Multi-factor Authentication method when absolutely needed - avoiding adding any additional friction unless needed.
Breached password detection
Strivacity provides a Breached Password service that can perform risk analysis against a customer password. This helps protect against:
1) Credential stuffing attacks - in the event that a customer is trying to use/re-use a password with their same identifier where that password has been previously breached, Breached Password Detection will prevent them from re-using that password and will disallow that breached password from being used.
2) Account take over - in the event that a customer's identifier and password are part of a known breached corpus, Breached Password Detection will prevent them from re-using that password and will disallow that breached password from being used.
Breached Password Detection's analysis of customer passwords occurs at any of the following points in the account lifecycle:
1) During customer registration (customer attempts to provide a previously breached password)
2) During a password reset (customer attempts to re-use a previously breached password)
3) During a customer password change (customer attempts to re-use a previously breached password)
4) During an administrative password reset or change (via the Admin Console)
Updated 5 months ago
