Default password policy
Learn more about Strivacity's default password policy and how it can mitigate common risks to passwords.
Strivacity comes pre-configured with a default password policy that is aligned to the 2019 NIST 800-63 Password Guidelines.
The Default Password Policy is automatically assigned on a per-Identity Store basis and is automatically assigned to the Default Identity Store from the moment that you start using the product, i.e. there is nothing that you need to do to ensure some password best practices are enforced for your customer accounts.
Strivacity comes pre-configured with a default password policy that is aligned to the 2019 NIST 800-63 Password Guidelines.
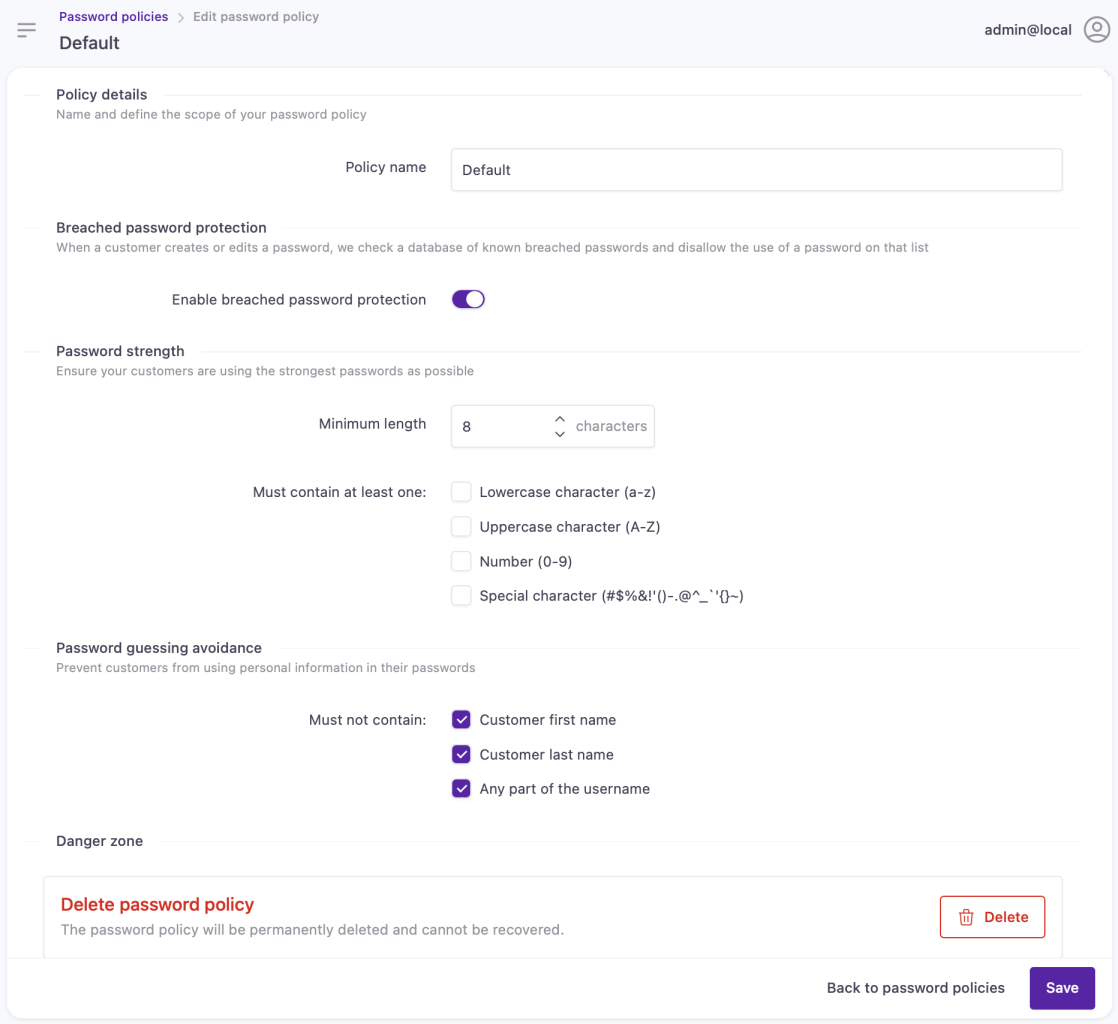
Default password policy settings
The default password policy is automatically assigned on a per-Identity Store basis and is automatically assigned to the default-identity-store from the moment you start using the Admin Console.
Here's our out-of-the-box password policy configuration:
| Setting | Default Value | Description |
|---|---|---|
| Breached password protection | Enabled | Prevents customers from using passwords that previously appeared in known data breaches. Customers can continue only if they've provided a password that hasn't been exposed. |
| Password strength | Disabled | NIST's 2019 Password Guidelines, it's public knowledge that complexity requirements are the least effective approach to produce secure passwords, so they're switched off in our default password policy. |
| Password guessing avoidance | These settings reduce the attack vector of cyber attackers leveraging customer-identifying information. You can find out more about password guessing avoidance here. | |
| First name | Enabled | Prevents customers from using word-character strings longer than 4 characters from their first name. |
| Last name | Enabled | Prevents customers from using word-character strings longer than 4 characters from their last name. |
| Any part of the username | Enabled | Prevents customers from blending in parts of their username into their password. |
| Repeated character restriction | Disabled | Defines how many times a character is allowed to repeat consecutively in a password. The default count is set to 2 which means the same character is allowed to repeat twice e.g. 'aa', but 'aaa' is not allowed. The restriction is case sensitive which allows the lower and upper case of the same letter to alternate e.g. 'aAA', 'aaA', etc. |
| Sequential character restriction | Disabled | Limits the length of character sequences in a password. The default count is set to 2 which prevents the use of character sequences longer than 2, e.g. '12' is allowed, but '123' can't be used. |
| Password reuse restriction password count | Disabled | Prevents the re-use of recent passwords. If enabled, users are not allowed to pick passwords they used the last set number of times. The default count is set to 10. |
| Password reuse restriction period | Disabled | Prevents the re-use of passwords from a recent time range. This restriction can make sure that users won't keep resetting their passwords until they bypass the password count based re-use restriction. The default period is set to 3 days. |
| Password age restriction | Disabled | Defines the maximum age of passwords. Users will be required to change their password after the specified lifetime is up. The default period is set to 30 days. |
While the 2019 NIST 800-63 Password Guidelines do not recommend any password complexity requirements, please note that password policies do support password complexity and more advanced password options. You can view Password Policies for more information.
Updated over 1 year ago
