Multi-factor methods for administrative accounts
Add multi-factor authentication methods to the authentication journey for your administrative staff to enroll in.
Authentication methods & factors
One-time passcode & Magic Links
You can enable temporary one-time authentication factors that admins can receive via email, SMS, or a voice call.
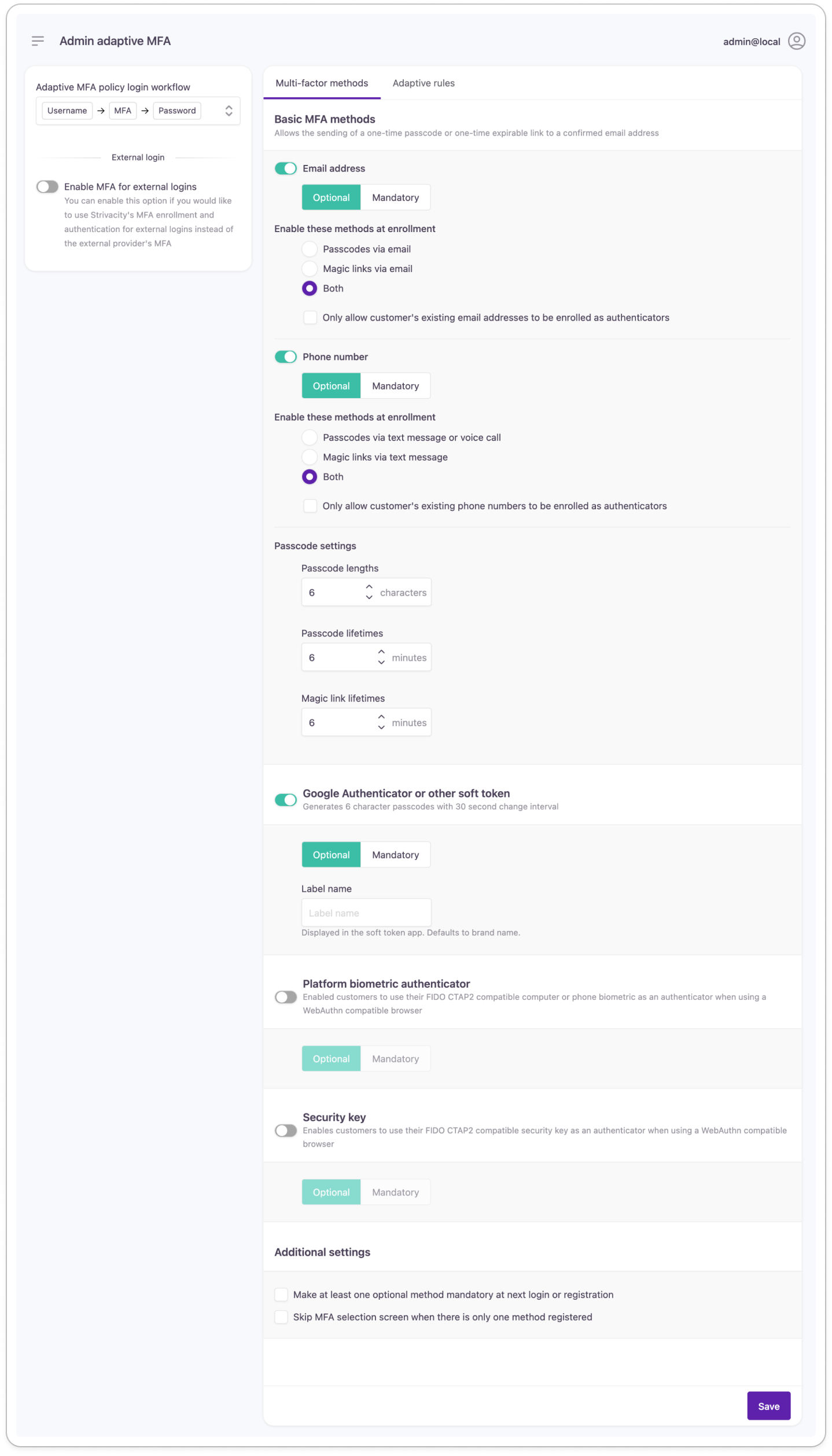
Email authenticator
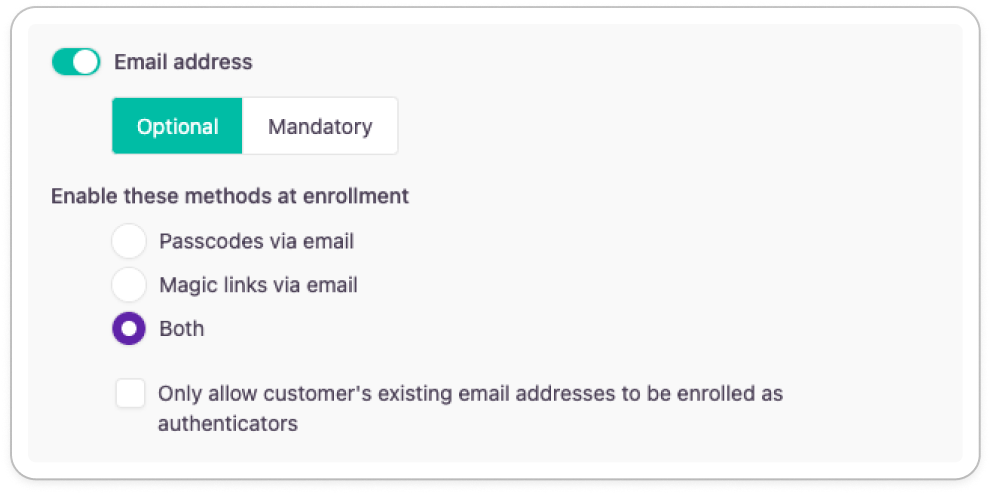
Phone authenticator
Email factors
- Passcodes via email: sends a one-time passcode.
- Magic links via email: sends an expirable link.
Phone factors
- Passcode via text message or voice call: sends a one-time passcode by default, or initiates a voice call per request. Admins can ask for a voice call in their authentication workflow.
- Magic links via text message: sends an expirable link.
Factor restriction
At each method, select which factors can be used for secondary authentication.
Authenticator restriction checkboxes
You can restrict admins to enroll only the email address(es) or phone number(s) as authenticators that are already added to their accounts.
Parameters
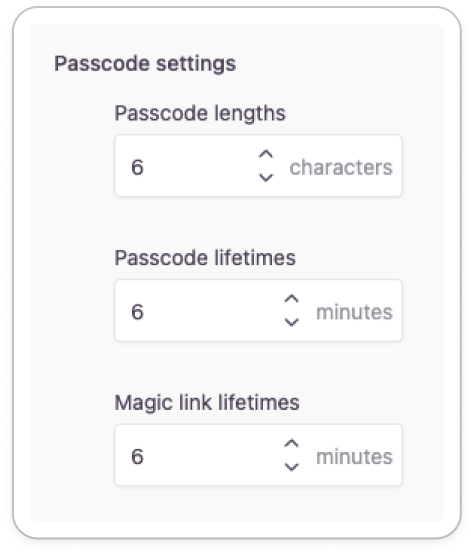
| Passcode Lengths | You can specify the character length of the one-time passcodes for both email and phone number-based methods in this field. Recommended minimum length: 6 characters (digits) by default. Maximum length: 8 characters. |
| Passcode Lifetimes | You can specify the character length of the one-time passcodes for both email and phone number-based methods in this field. Recommended minimum length: 6 characters (digits) by default. Maximum length: 8 characters. |
| Magic Link Lifetime | You can enter the lifetime of Magic Links for both email and phone-based methods here. The lifetime of a Magic Link starts from the time the passcode has been sent out. Strivacity invalidates the Magic Link once its lifetime has been exceeded. In this case, admins will have to restart the login process. |
Soft token authenticator apps
You can enable the Google Authenticator or other soft token authenticator apps as an additional authenticator option for your administrative staff. Renewable one-time passcodes will be available via the application.
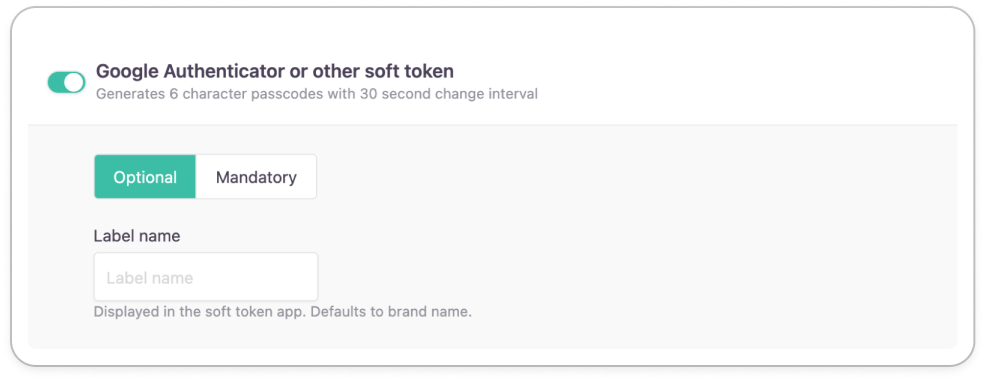
Label name
You can add a display name that will appear above the soft token in the authenticator application. This label helps admins in finding the right passcode in the authenticator app.
FIDO2 support
You can offer FIDO2-based authentication options for your admins by enabling platform biometric authentication or security key enrollment.
Platform biometric authenticator
If enabled, you allow admins to enroll the biometric information stored on their personal devices as an authenticator.
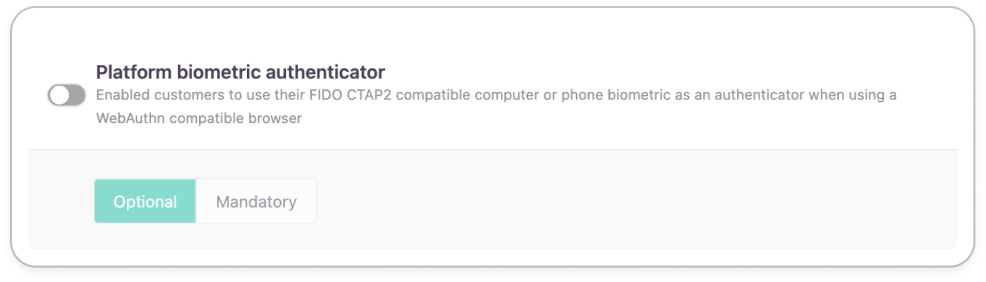
The customer's enrollment and authentication experience will slightly vary depending on the biometric security system they have installed in their devices.
Security key
If enabled, you allow customers to enroll a roaming authenticator such as a security key (YubiKey, Titan Security Key) or a FIDO-compliant mobile device as an authenticator.
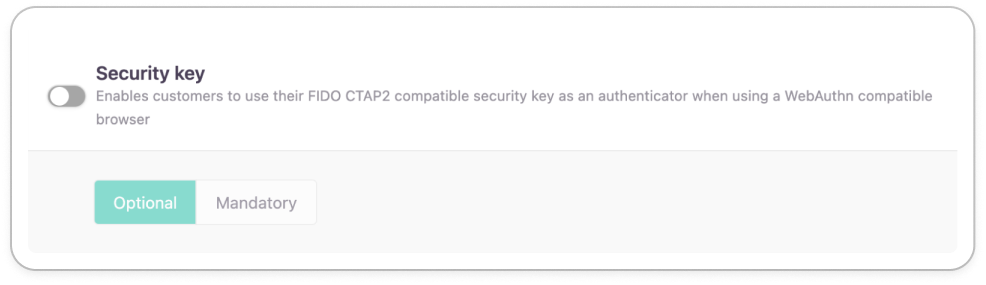
The customer's enrollment and authentication experience will slightly vary depending on the browser and OS the customer is using.
Passkey
If enabled, customers will have the option to authenticate using a passkey.
Passkeys provide a secure and customer-friendly alternative to traditional password and MFA methods. Passkeys allow two factors of authentication—something you have (your device) and something you are (your fingerprint or face)—to be combined in a single step, eliminating the need for passwords or less secure and convenient methods like email and SMS.
MFA enrollment configuration
Multi-factor method controls allow you to various enrollment options for admins or require them to in one or multiple authentication methods.
Optional MFA
You can leave it up entirely to admins to switch on MFA in their accounts by leaving enabled MFA methods optional.
One multi-factor method always needs to be enabled for your adaptive access workflow.
Admins can manage factors for each enrolled authentication method on their 'My Account' page:
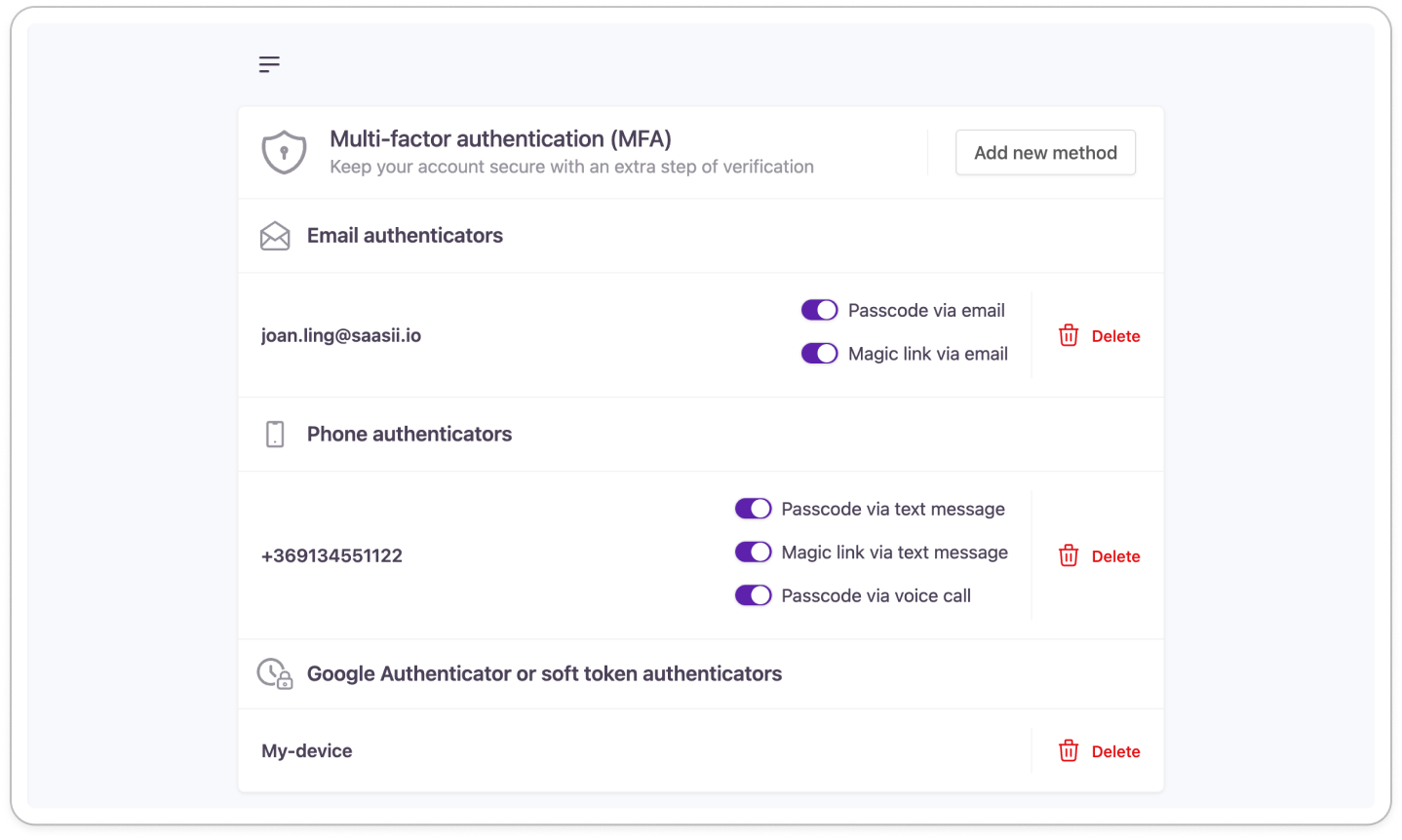
Make at least one optional method mandatory at the next login or registration
When selected, admins will be required to enroll in one of the optional authentication methods.
This option is only available if there are no mandatory methods selected.
Mandatory MFA
You can require admins to enroll in specific MFA methods to enhance the security of their accounts.
If multiple MFA methods are mandatory, admins will be required to enroll in each method in the following order: email authentication first, then phone authentication if mandatory, then soft token authentication if mandatory, etc.
After successful enrollment for each mandatory method, admins will only be stepped up to one of the enrolled methods during future logins.
Updated over 1 year ago
