Authenticate step
The Authenticate step takes place after customer identification and before any progressive profiling or additional required MFA registrations in the login journey. It validates the customer's credentials and determines whether additional authentication steps, such as multi-factor authentication (MFA), are necessary.
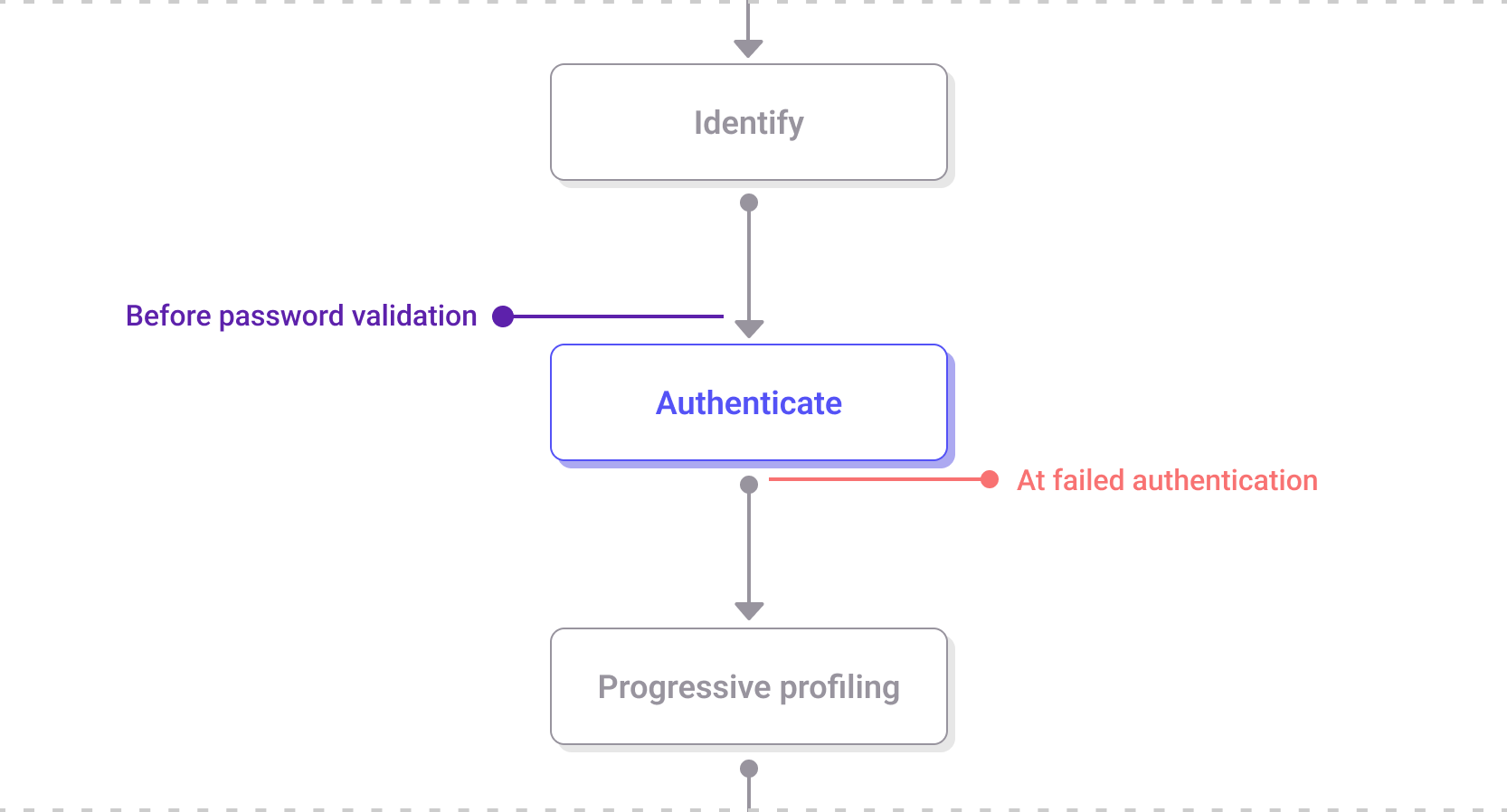
The Authenticate step within the login journey
Key features of the Authenticate step
-
Governed by Adaptive Access policies
The authentication workflows are dictated by the Adaptive Access policy. These workflows define the sequence and type of authentication methods required, which can include:- Identifier ➔ MFA ➔ Password
- Identifier ➔ Password ➔ MFA
- Identifier ➔ MFA (Passwordless)
- Identifier ➔ Password (Single factor)
"Identifier" refers to collecting and verifying an identifier, "MFA" represents a non-password-based authentication step, and "Password" involves collecting and verifying a password.
-
Passwordless options
Passwordless authentication can be achieved through various methods, such as:- Configuring Adaptive Access policies that exclude password steps.
- Utilizing "keep me logged in" functionality for sessions within the inactivity timeout period.
- Suppressing the password step using lifecycle event hooks.
- Offering passkeys as a passwordless authenticator.
-
Skipping the MFA step
The MFA step may be skipped in these scenarios:- Adaptive Access policies that omit MFA.
- Policies that include MFA but do not trigger step-up rules.
- Suppression via lifecycle event hooks.
Screens in the Authenticate step
Password challenge
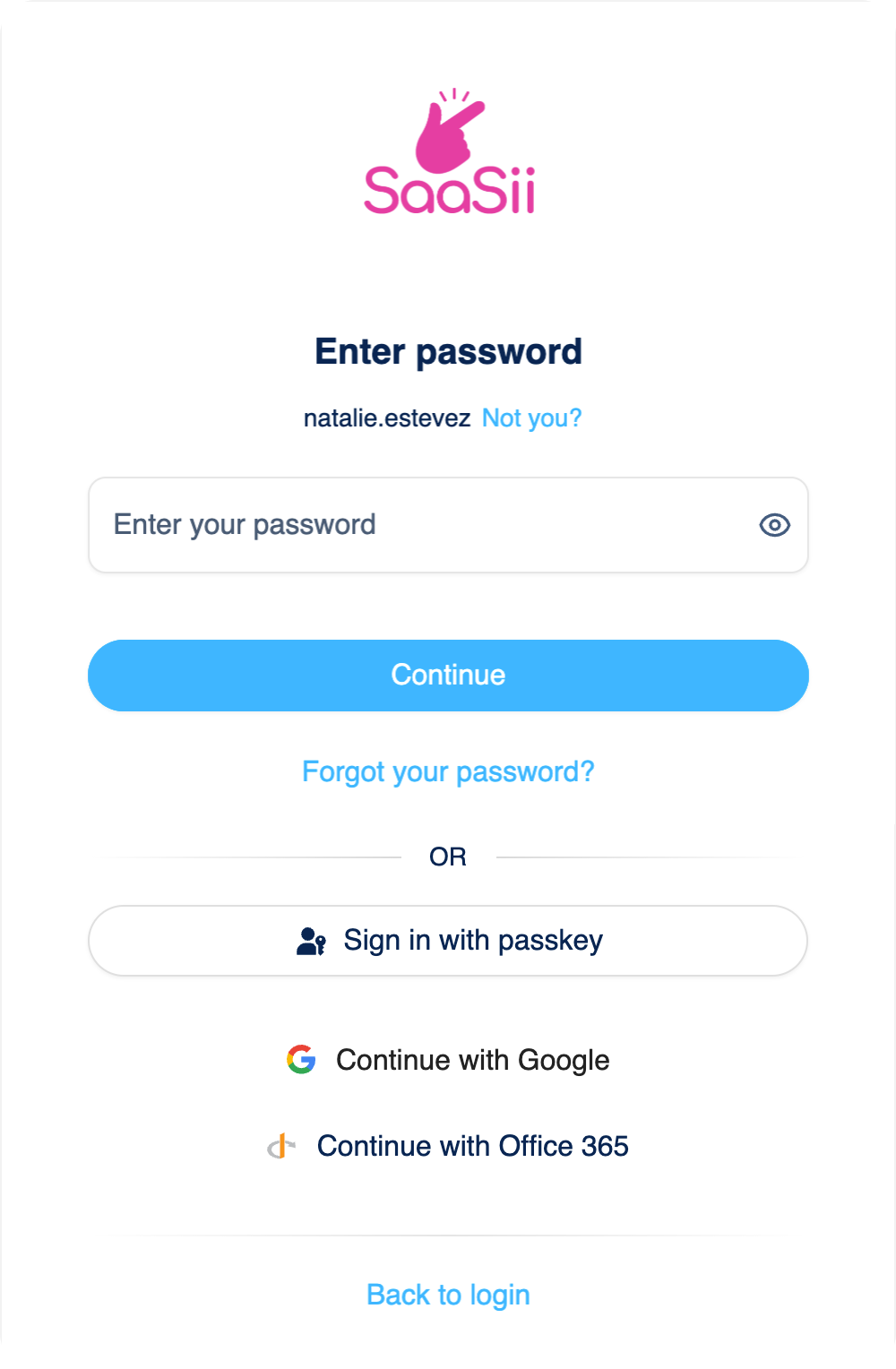
Password challenge screen
The password challenge screen is where customers authenticate by entering their password, with additional options like editing the identifier, resetting the password, or using alternative methods if configured.
Screen elements
- Identifier:
- Displays the identifier being authenticated.
- Includes an "edit identifier" option ("Not you?") that:
- Links back to the identifier screen if no accounts are remembered.
- Links back to the account chooser if one or more accounts are remembered.
- Password input:
- Captures the password.
- The password is masked by default, but can be unmasked by the customer if needed.
- "Keep me logged in":
- Configured to display in the application settings.
- Allows customers to remain logged in without re-entering their password during the inactivity timeout period.
- Continue button:
- Proceeds the customer to the next screen in the login process.
- Forgot your password:
- Displays when:
- Enabled in the Self-Service policy.
- The customer has an email or phone identifier that can be used as a recovery target (email or phone).
- In username-only identity stores, a confirmed email or phone number can act as a recovery target, or the Adaptive Access policy permits non-confirmed targets.
- Displays when:
- External login button:
- Can appear if the customer bypassed the identifier screen but has a linked external account they can use to log in.
- Back to login:
- Displays when a login URL is defined for the client.
- Selecting it restarts the login process.
MFA method chooser
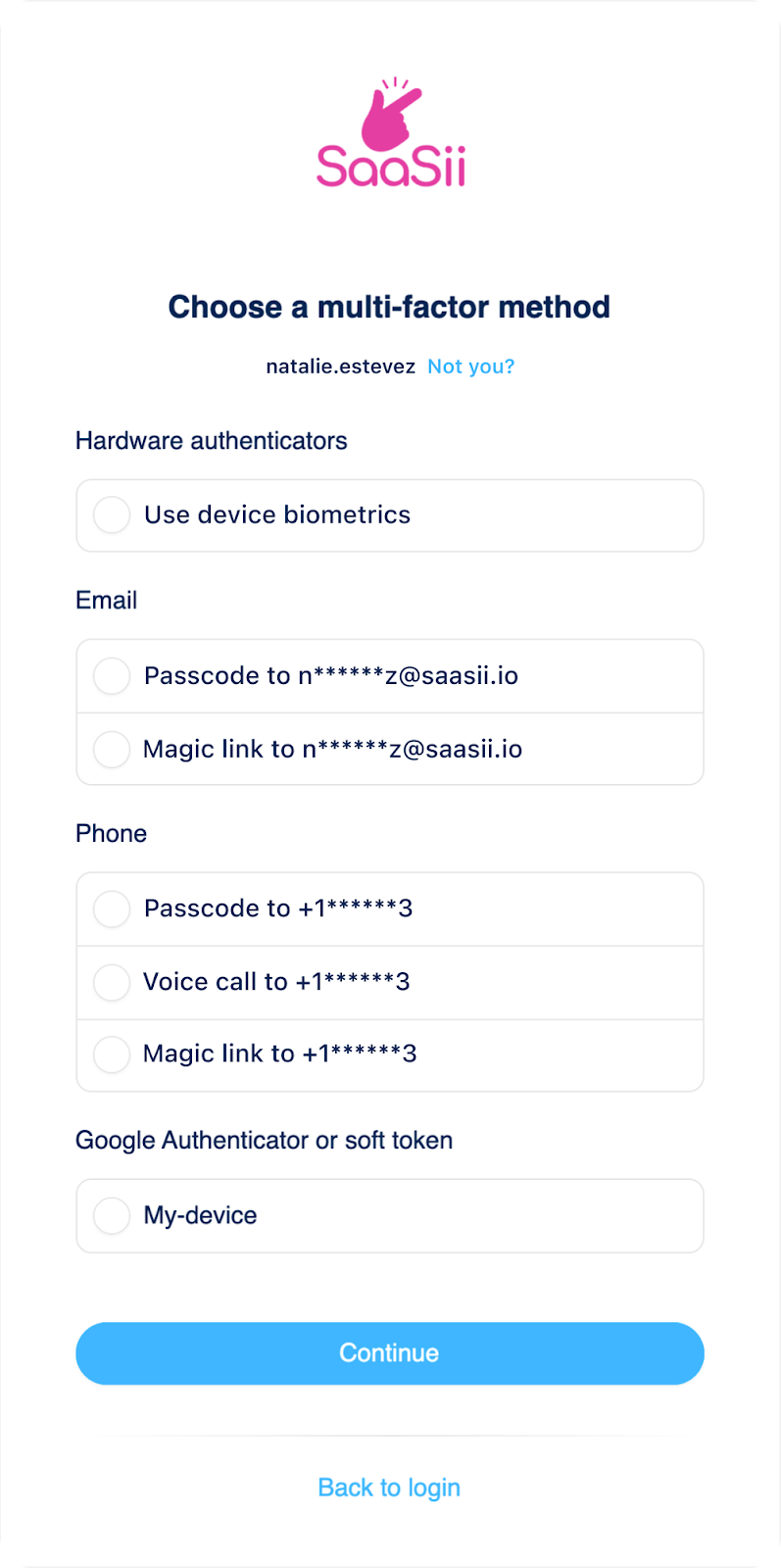
MFA method chooser screen
The MFA method chooser screen allows customers to select an available multi-factor authentication method based on the options determined by the Adaptive Access policy.
- MFA options: The adaptive access policy defines which authenticators are available for the customer to use during authentication.
- Masked identifiers: Phone numbers and email addresses are partially masked to ensure they are recognizable to the owner but useless to potential threat actors.
- “Remember this device for 30 days”:
- Displays when device recognition is enabled as a step-down rule in the adaptive access policy.
- The duration is adjustable, and the default selection state can also be configured.
-
MFA challenges
- One-time passcodes (OTP): Sent via email or phone; previous codes are invalidated when a new one is sent.
- Magic links: Sent via email or phone; new links invalidate prior ones.
- Security keys: Requires FIDO2-compatible keys and relies on OS/browser interfaces.
- Passkeys: A seamless, passwordless authentication method.
Branding
The Authenticate step supports customization and branding:
- Screen elements: Logos, titles, and content areas are configurable through the Branding policy.
- Notification policies: Customizable templates for notifications sent during MFA challenges.
Extensibility points
During the Authenticate step, the following extensibility points are available:
Before password validation: This event is triggered when a customer's account doesn't have a password authenticator yet. This hook can retrieve the password from an external identity store if the customer's account was migrated, and reset the password in the Strivacity identity store with the migrated password. The hook also allows for the validation of the password through an external system without having to store it in the Strivacity identity store. Synchronous hook.
At failed authentication: This event triggers when customer authentication or registration fails. This hook provides the reason for the failure, allowing you to customize the error returned, display an error page with a custom message, or redirect the customer based on the failure context. Synchronous hook.
To learn more about extensibility points, refer to the Lifecycle event hooks documentation.
Updated 6 months ago
