Splunk configuration
With event streaming, you can configure Strivacity to send audit logs and account events to Splunk. This allows you to monitor activity, create dashboards, and set up alerts in line with your existing data workflows.
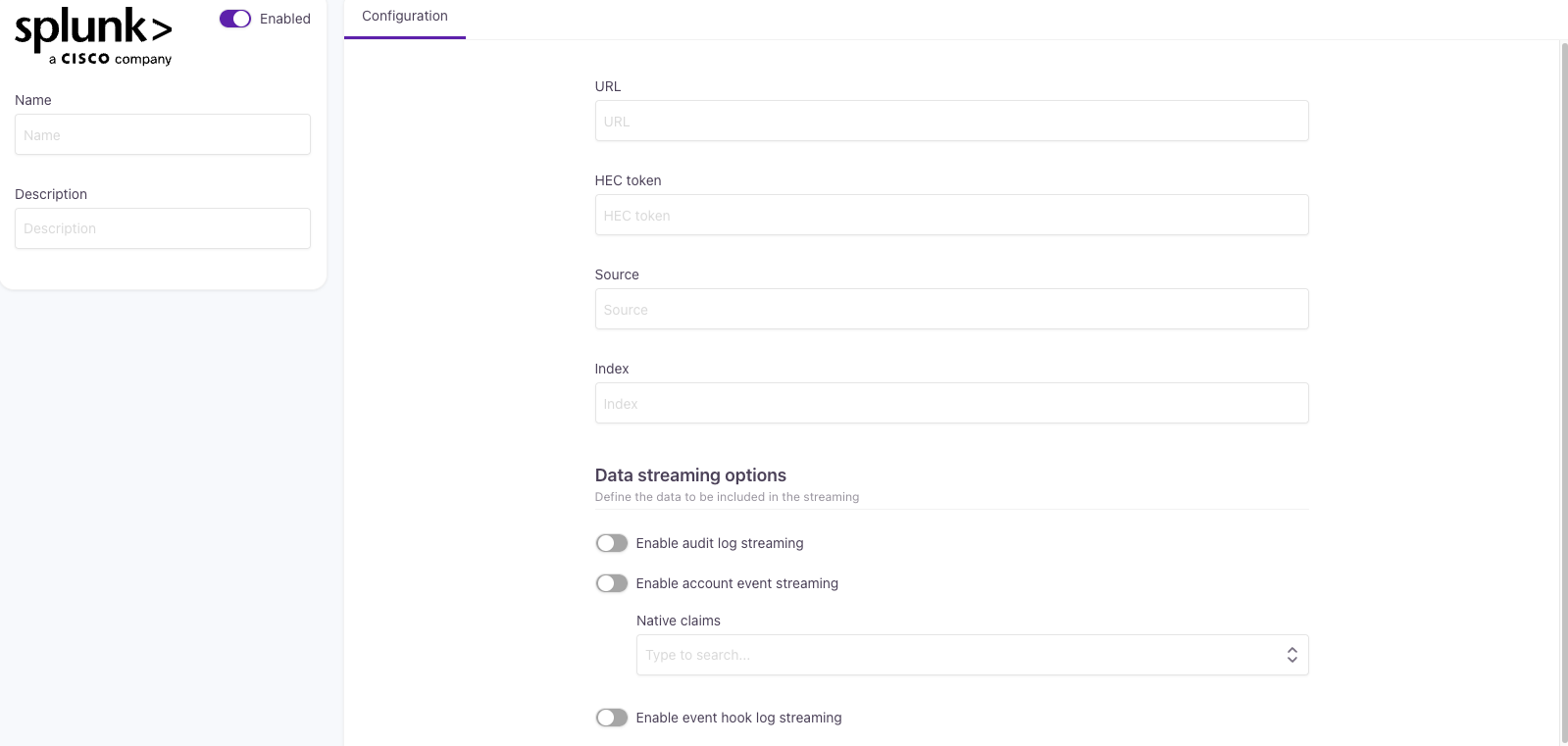
Configuring event streaming to Splunk
When creating a Splunk configuration, you will be asked for the following information:
| Field | Description |
|---|---|
| Name | A name for your Splunk configuration. |
| Description | A brief description. |
| URL | The HTTP Event Collector (HEC) endpoint in Splunk (for example, https://<your-splunk-host>/services/collector/event). |
| HEC token | Your Splunk HEC token used for authentication. |
| Source | (Optional) Sets the source field in Splunk. |
| Index | (Optional) Sets the index in Splunk where events will be stored. |
Data streaming options
- Enable audit log streaming
Sends the entire audit log to Splunk. Certain policy changes (for example, Branding policy, Notification policy, and Lifecycle event hooks) may appear with empty request and response fields. - Enable account event streaming: Sends customer-centric events (for example, login attempts, password changes) to Elasticsearch.
- Limited to the basic information available in the header of an account event. This means that only high-level details are forwarded, such as the customer’s identity, the timestamp of the action, and labels indicating success or failure. The detailed steps (for example, identification started, MFA selection started) are not included by default.
- If additional account information is required, you can enable native claims. These native claims are selected via a UI field that lists all native claims available in your instance and included in the event payload when enabled.
- Enable event hook streaming: Sends logs generated by Lifecycle event hooks as part of account events. This option provides visibility into hook execution without accessing hook code directly.
Splunk event format
Strivacity sends events to Splunk in JSON format compatible with the Splunk HTTP Event Collector. A typical JSON payload looks like this:
{
"time": 1638316800,
"host": "my-strivacity-domain.com",
"source": "strivacity",
"sourcetype": "json",
"index": "main",
"event": {
// Account event or audit log data goes here
}
}
- time: The UNIX timestamp of the event.
- host: Your Strivacity instance domain.
- source: Optional field you can configure; can also be set in Splunk.
- sourcetype:
json. - index: An optional index name (can also be configured in Splunk).
- event: Contains the actual event data from Strivacity, including customer details (excluding any actions that are not relevant for streaming).
Once saved, Strivacity will begin sending events to your Splunk instance. You can then use Splunk to monitor, search, and create dashboards based on these events.
Updated 5 months ago
